CSRF(Cross-Site Request Forgery)

Understanding CSRF.
CSRF attacks occur when a malicious actor tricks an authenticated user into unknowingly performing actions on a web application that they are authorized to perform. This is typically achieved by exploiting the user's active session on the vulnerable site. The attacker crafts a malicious request and lures the user into executing it, often through social engineering techniques like phishing emails or malicious links.
How Does CSRF Work?
- Authentication: The victim user is authenticated to a trusted website, for example, a banking site.
- Exploitation: The attacker lures the victim to visit a malicious website or click on a crafted link.
- Unauthorized Action: The malicious website or crafted link contains requests that execute actions on the trusted website, using the victim's authenticated session.
- Execution: The browser automatically sends the authenticated requests, as it includes cookies for the trusted website, without the user's knowledge.
Example Scenario.
Let's say a victim is logged into their online banking account. The attacker sends them an email with a link to a malicious website. On that website, there's a hidden form that automatically submits a request to transfer money from the victim's bank account to the attacker's account. When the victim visits the malicious site, their browser, without their knowledge, sends the request to the bank's website because the victim is already authenticated there.
Recap:
Understanding CSRF Attacks
CSRF attacks occur when a malicious actor tricks an authenticated user into unknowingly performing actions on a web application that they are authorized to perform. This is typically achieved by exploiting the user's active session on the vulnerable site. The attacker crafts a malicious request and lures the user into executing it, often through social engineering techniques like phishing emails or malicious links.
Common causes of CSRF.
Now that we understand CSRF let's understand these vulnerabilities which can be crucial for testing and flagging potential risks in web applications:
Lack of CSRF Tokens: CSRF tokens are unique tokens generated for each user session and included in HTML forms or AJAX requests. Without these tokens, it becomes easier for attackers to forge requests. Websites or web apps that don't use CSRF tokens to validate whether a request originates from an authenticated user's session are vulnerable. CSRF tokens add an extra layer of security by ensuring that the request is coming from an authorized source.
Predictable Request Parameters: If request parameters are predictable, attackers can craft malicious requests more easily, especially for GET requests where parameters are visible in the URL. If request parameters are predictable or easily guessable, attackers can craft malicious requests and trick authenticated users into unknowingly executing them. This is especially true for GET requests where parameters are visible in the URL.
No Same-Origin Policy Enforcement: Failure to enforce the Same-Origin Policy allows malicious sites to make requests on behalf of the user to the vulnerable site. Failure to enforce the Same-Origin Policy allows malicious sites to make requests on behalf of the user to the vulnerable site, potentially leading to unauthorized actions being performed.
State-Changing Requests: CSRF attacks typically target state-changing requests, such as updating user settings or making transactions, which are not properly authenticated. CSRF attacks typically target state-changing requests, such as updating user settings, transferring funds, or changing passwords. Websites or web apps that don't properly authenticate these requests are at risk.
User Session Management Issues: Weaknesses in how user sessions are managed, such as session fixation vulnerabilities or session prediction, can be exploited by attackers to execute CSRF attacks. Weaknesses in how user sessions are managed, such as session fixation vulnerabilities or session prediction, can be exploited by attackers to execute CSRF attacks.
Insecure Cross-Origin Resource Sharing (CORS) Configuration: Misconfigured CORS policies can allow unauthorized sites to make cross-origin requests, which can be leveraged in CSRF attacks. Misconfigured CORS policies can allow unauthorized sites to make cross-origin requests, which can be leveraged in CSRF attacks.
Lack of Proper Input Validation: Failing to properly validate and sanitize user input can lead to vulnerabilities like XSS, which in turn can be exploited to execute CSRF attacks.
Example CSRF Attack
Lets do a quick guide of an exploit in action.
For this we will use our labs at hackxpert.com, lets use the credit transfer app we have set up, you can find it here
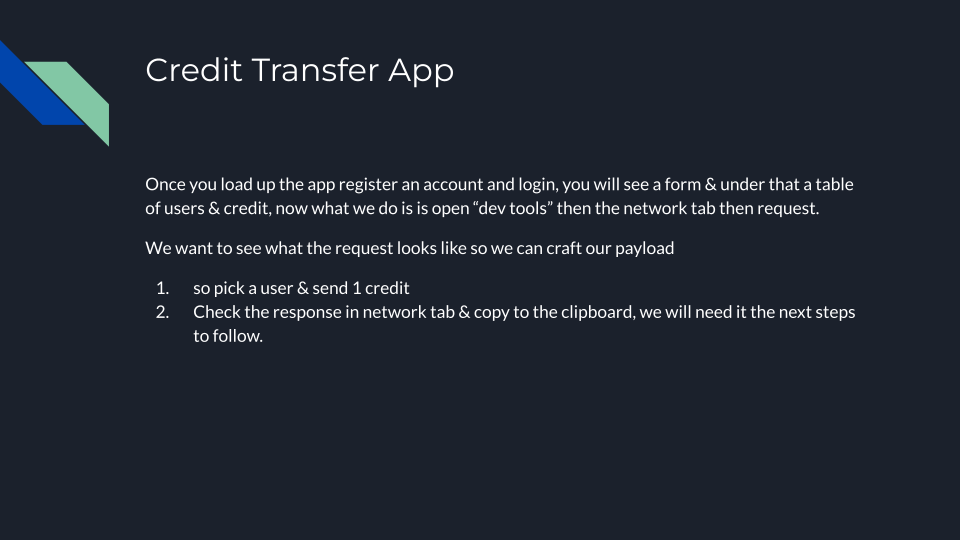
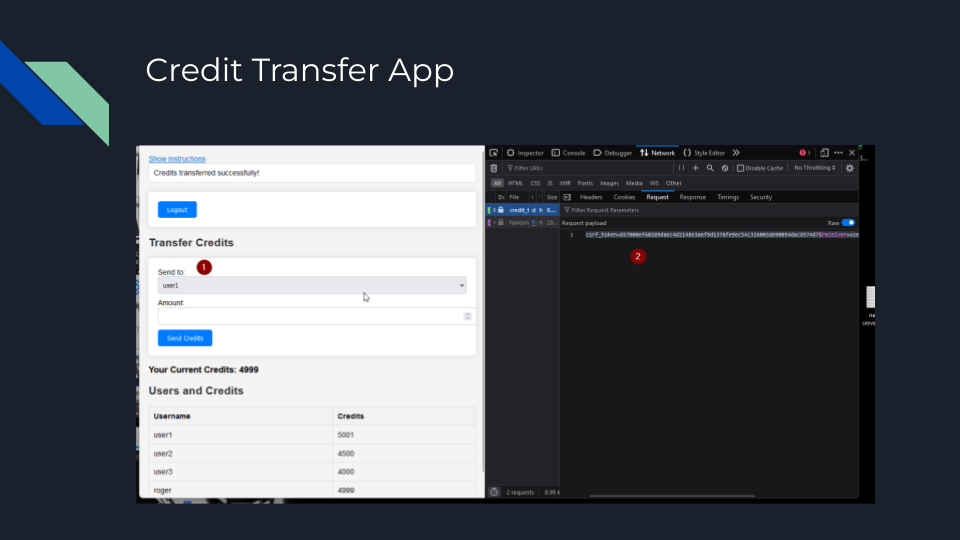
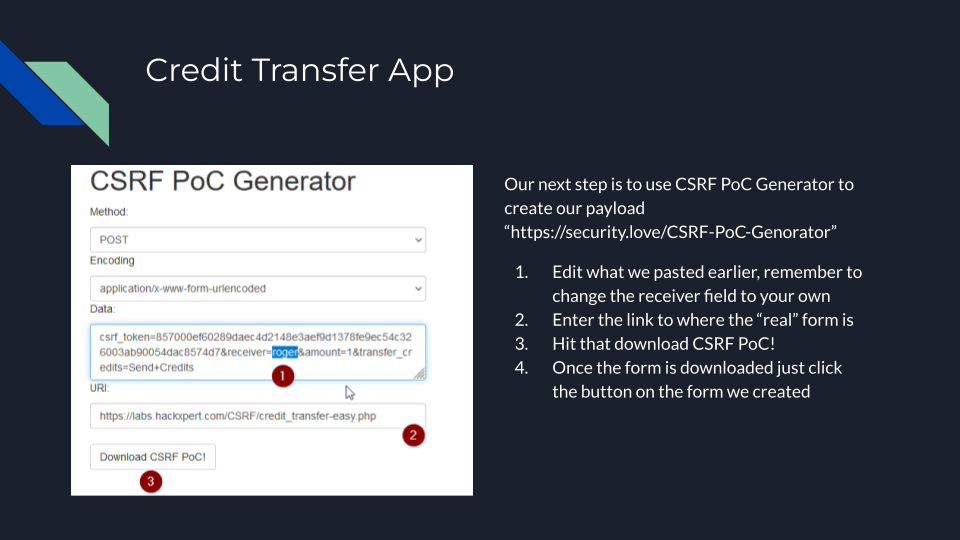
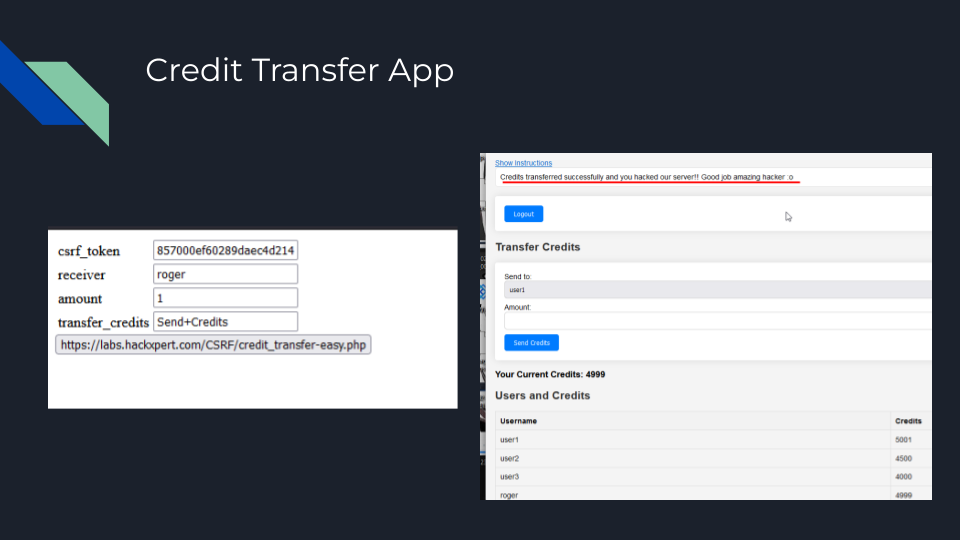
CSRF in the wild is not as easy as shown here, but when testing its worth trying the easy one first as you never know.
Happy Hunting !
